Duties Owed: Low-Intensity Cyber Attacks and Liability for Transboundary Torts in International Law
abstract. Low-intensity state-sponsored cyber attacks exist within a “gap” in public international law. Falling short of the definitions of use of force and intervention, these attacks are not clearly governed by international law. Some scholars have sought to stretch established international legal categories to resolve this problem, while others have suggested new treaty regimes for cyberspace altogether. I suggest an alternative: liability for the duty to prevent and redress transboundary harms. By examining the origins of this duty, this Note identifies how liability for the duty to prevent and redress transboundary harms might apply for low-intensity cyber attacks, an increasingly common and destructive category of attacks.
author. Yale Law School, J.D., expected 2018; University of Cambridge, M.Phil., 2015; Harvard College, A.B., 2014. I am grateful to Professor Oona Hathaway and Professor Harold Koh for their support and guidance throughout the writing of this piece. I would also like to offer sincere thanks to S.J. Calum Agnew, Rebecca Crootof, and Asaf Lubin, without whom this project would have never gotten off the ground. Thank you to Joe Falvey and the Yale Law Journal Notes Committee, Ido Kilovaty, and Professor Jack Goldsmith, all of whom provided helpful comments, insights, and suggestions. Finally, I would like to express my deepest appreciation for the host of generous mentors who have guided me over the years. All errors are mine alone.
introduction
On November 24, 2014, a menacing red skull flashed on every employee’s screen at Sony Pictures Entertainment’s headquarters in Culver City, California. The attackers, calling themselves the “Guardians of Peace,” scrubbed more than one hundred terabytes of Sony’s data and leaked thousands of confidential documents.1 The attackers threatened to release more documents if Sony did not stop the release of The Interview, Sony’s newest political-satirical film on North Korea, and made clear their intention to cause further harm and even violence.2 In the end, many theaters caved to the attackers’ demands, refusing to screen the film—but not before the attacks resulted in tens of millions of dollars in damage,3 including the destruction of Sony data systems,4 the corruption of thousands of computers,5 the loss of millions of dollars in revenues,6 and leaked trade secrets.7
In the aftermath of the attack, the U.S. government made an unprecedented accusation, officially attributing the Sony attack to the government of North Korea.8 After an FBI investigation that linked the attack’s code, infrastructure, and overall design to previous attacks that were believed to have been carried out by North Korea,9 the State Department officially condemned North Korea on December 19, 2014.10 In a special press release, President Obama vowed that the United States would respond proportionally in the arena of its choosing.11
International legal and technology experts have since hotly debated the attribution of the Sony attack. Some have claimed that the United States misattributed or prematurely attributed the attack to North Korea.12 Others have noted that the United States’s actions could set a dangerous precedent.13 In any case, observers recognize that the United States’s response was a key example—now one of a steadily growing number14—of a state officially accusing another of a cyber attack.15 Yet even if attribution is possible, a more pressing question for international law emerges: what international law has North Korea violated by committing this attack?
As surprising as it may seem, the traditional international legal perspective seems to answer “none.”16 Despite the increasingly common and destructive nature of state-sponsored cyber attacks,17 it is difficult to locate the precise source of illegality for these “low-intensity” cyber attacks.18 In the language of the Draft Articles on State Responsibility, states are only responsible for acts attributable to the state that are “wrongful” under international law.19 Low-intensity state-sponsored cyber attacks do not fit this bill. Scholars have recognized this “gap” for low-intensity cyber attacks and sought solutions. Some have tried to broaden current international legal categories of impermissible conduct to cover these attacks.20 Others have declared that a new treaty or legal regime is needed before international law can render low-intensity attacks wrongful.21 Neither approach has proved satisfactory thus far.
This Note proposes an important theoretical and practical alternative that derives from a preexisting but underutilized source of international law: liability for transboundary harm. Liability in international law is a complicated, controversial, and often misunderstood concept that has developed separately from, but directly feeds into, the customary international legal regime of state responsibility. Liability does not emerge from a violation of international law per se, which would constitute wrongfulness (or even give rise to international criminal responsibility), but rather, simply from an act of harm.
In particular, liability in international law derives from the customary duty to prevent and redress transboundary harm. This duty is most familiar in the environmental realm,22 despite its roots in and application to a broader range of legal issues.23 International liability for a violation of this duty is triggered by the “transboundary movement of...harmful effects” above a certain level of severity not traditionally tolerated,24 and involving a causal relationship between the damage caused and the activity causing it.25
To make the case for applying this liability approach to low-intensity state-sponsored cyber attacks, this Note proceeds in four Parts. Part I begins by explaining why low-intensity cyber attacks appear to escape regulation under existing international legal obligations. Part II next examines the origins of the duty to prevent and redress transboundary harm, which forms the basis of international liability, and the complex relationship between liability and the doctrine of state responsibility. Part III applies liability for this duty to low-intensity, state-sponsored cyber attacks. Part IV then turns to the three key benefits of a liability approach for cyber attacks: (1) pragmatic appeal to states’ interests and emphasis on the duty to redress harms, (2) clarification of the literature on due diligence and countermeasures in international law, and (3) acknowledgement of duties owed to third parties. This Note ultimately proposes that liability for transboundary harm offers a fruitful approach for bringing low-intensity cyber attacks into the fold of international law.
i. The Puzzle of Low-Intensity State-Sponsored Cyber Attacks
Before turning to liability for transboundary harm and how it might apply in the cyber realm, this Part describes the problems posed by low-intensity cyber attacks and why established international legal principles have proven incapable of regulating these attacks.
A. The Problem
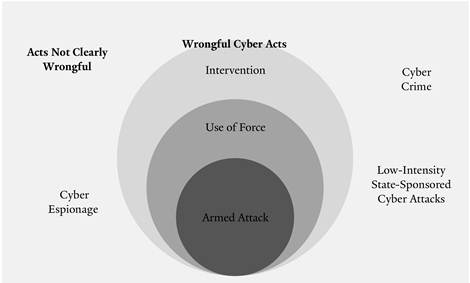
A cyber attack is “any action taken to undermine the functions of a computer network for a political or national security purpose.”26 Low-intensity cyber attacks, specifically, encompass any of a wide range of actions taken to “alter, disrupt, deceive, degrade, or destroy” computer systems or networks resulting in destruction and coercion insufficient to amount to a use of force or intervention under international law.27 As the latter half of this definition makes clear, defining low-intensity cyber attacks inevitably involves a discussion of what they are not: actions clearly governed by established international legal rules. Here, I briefly explain why low-intensity cyber attacks merit attention and why bringing law to bear on them is a worthwhile goal in the first place.
First, low-intensity cyber attacks are incredibly costly. Experts suggest that the average large U.S. company spends more than $7.7 million on preventing and responding to cyber attacks each year, a relatively high amount compared to that spent by large foreign companies.28 Around the world, the numbers are similarly startling: cyber attacks result in more than $400 billion in losses to companies each year,29 and potentially as much as $2.1 trillion in losses by 2019.30 While governments and private entities have dramatically boosted their cyber security in recent years, experts remain convinced that even the best security precautions remain incapable of eliminating all vulnerability to future attacks.31 This is troubling, given that even a single vulnerability can open the door to considerable destruction; the attack on Sony, for instance, resulted in the destruction of three thousand computers and eight hundred servers.32
Moreover, low-intensity cyber attacks are incredibly common. While much scholarly attention has focused on the threat of major cyber attacks that border on acts of war, the most common cyber attacks fall considerably below this level. In 2015, only 2.4% of all cyber attacks were conducted in the context of war or gave rise to a degree of physical damage approaching a use of force.33 In fact, experts agree that “[f]ew, if any, cyber operations have [ever] crossed the armed attack threshold.”34 The need for legal restrictions on and remedies for cyber attacks is no less severe given the immense impact that these attacks have on personal and state property.
Third, even if it were possible to expand existing categories of law to encompass low-intensity cyber attacks, doing so could create havoc in other areas of law. As the next Section and Part IV explain, expanding the concepts of non-intervention and sovereignty in international law could result in problems for NGOs and other supporters of human rights who engage in political activities abroad. Such an expansion would also complicate our understandings of which routine cross-border infringements constitute violations of international law.35
Depending on how existing bodies of international law are broadened, states might also either lose the right to respond “in kind” to low-intensity cyber attacks, or conversely, gain the right to respond with disproportionately numerous counterattacks.36 But such measures may be unsustainable, as escalations are likely to mount over time if states are permitted to respond to low-intensity attacks without restriction. For instance, after the Sony attack, it appears likely that a portion of North Korea’s internet was temporarily knocked offline although it is unclear who mounted the response.37 Like the initial Sony hack itself, such counterattacks are, by their nature, difficult to control. Subsequent miscalculations, human coding error, and varying perceptions of the damage can lead a response to cause even greater destruction and more severe legal consequences than was initially intended.38 Nevertheless, the alternative—leaving low-intensity cyber attacks unaddressed—may also have a corruptive effect on the international legal order.39 By encouraging self-help, unfriendly action, and non-cooperation, this option has the potential to blur the fundamental boundary between peace and conflict and thereby generate heightened anxiety about future destruction.40
Therefore, a response to low-intensity cyber attacks is necessary, but as the next Section explains, an adequate response is unavailable under traditional legal frameworks.
B. The Gap in International Law
In this Section, I consider a number of legal rules that lack clear application to low-intensity cyber attacks, including international law on the use of force, intervention, armed conflict, and respect for state sovereignty.
The prohibition on the use of force—which the International Court of Justice (ICJ) has declared a “cornerstone of the United Nations Charter”—is the most natural place to look for international law applicable to low-intensity cyber attacks.41 Article 2(4) of the UN Charter proclaims, “All Members shall refrain...from the threat or use of force against the territorial integrity or political independence of any state, or in any other manner inconsistent with the Purposes of the United Nations.”42 While the scope of Article 2(4)’s prohibition on the use of force is hotly debated,43 the object and purpose of the UN Charter44 and its travaux préparatoires45 support a conclusion that Article 2(4) likely refers to “armed force,”46 or at least to incidents giving rise to significant physical damage.47 Adapting the prohibition on the use of force to cyber attacks, the Tallinn Manual on the International Law Applicable to Cyber Warfare (Tallinn Manual), a NATO-commissioned study produced by an international group of experts on the legality of cyber conflicts, has relied on this traditional approach. The Tallinn Manual reasons that only cyber attacks of sufficient “severity,” “invasiveness,” and “military character” amount to uses of force.48
In light of the Tallinn Manual and a growing consensus in favor of such an “effects-based” approach,49 low-intensity cyber attacks appear to escape prohibition under Article 2(4), because they typically fail to cause the extensive physical destruction necessary to meet the traditional definition of use of force.50 For example, while the Sony attack resulted in the destruction of more than three-quarters of Sony’s main studio computers,51 most scholars agree that this destruction is not comparable to destruction caused by kinetic operations and therefore is beyond the scope of use of force under international law.52
Second, unless low-intensity cyber attacks take place within the context of a preexisting international armed conflict, they are not clearly governed by the laws of armed conflict (jus in bello).53 Under international law, “armed attacks,” which encompass attacks involving the “most grave forms of the use of force,”54 trigger the right of a state to self-defense under Article 51 of the UN Charter, as well as the application of jus in bello.55 While some states, such as the United States, maintain that armed attacks are synonymous with mere uses of force,56 it is clear that low-intensity cyber attacks fall short of either a use of force or an armed attack, and thus do not give rise to jus in bello restrictions.57
Third, low-intensity attacks also fail to qualify as unlawful “interventions.”58 Customary international law suggests that an intervention requires “methods of coercion”59 “bearing on matters in which each State is permitted, by the principle of state sovereignty, to decide freely,” such as its “political, economic, social and cultural” system.60 Low-intensity cyber attacks struggle to meet this definition because they are typically targeted at private entities, create relatively localized harms within a state, and do not impact policy matters traditionally within the domaine réservé of the state61—a necessary element of “coercion” within the definition of intervention.62 While not every attack failing to meet the definition of the use of force falls outside of the definition of intervention, many do.63 The prohibition on intervention applies narrowly in cyber attacks, because intervention has routinely required more than mere “interference.”64 For example, Iran’s attack on the Sands Casino in 2014 resulted in more than $40 million in damage to the Las Vegas Sands Corporation from destroyed data and computer systems, yet the attack had no broader political impact.65
Fourth, low-intensity cyber attacks initiated by states do not constitute “cyber crime.” International criminal law applies only to individual actors, not states, and scant international criminal law is directly applicable to low-intensity cyber attacks.66 Nonetheless, state-sponsored cyber attacks typically remain “more advanced and dangerous” than routine cyber crimes carried out by non-state hackers.67 For this reason, Facebook and Google notify users when they believe accounts have been targeted or compromised by an attacker suspected of “working on behalf of a nation-state,”68 as opposed to mere individuals.
figure 1.
cyber acts in international law
 |
Recognizing that low-intensity state-sponsored cyber attacks fall beyond the bounds of traditional international law, some scholars have recently attempted—albeit with limited success—to apply broader customary international law principles to the low-intensity cyber arena. After all, within the doctrine of state responsibility, state action is wrongful when the conduct is “attributable to the State under international law” and “[c]onstitutes a breach of an international obligation of the State.”69 Finding a source of such breached obligations would not only deem low-intensity cyber attacks wrongful, but would also entitle injured states to seek cessation of the offense, reparation, assurances of non-repetition, and perhaps even countermeasures if the offense continues.70 These approaches, however, have struggled to proscribe low-intensity attacks as well.
For example, appeals to “sovereignty”71 and “territorial sovereignty”72 do not provide a firm legal basis for outlawing low-intensity cyber attacks.“Sovereignty” is difficult to apply in this context in part because some scholars and governments openly regard cyberspace as part of the global commons,73 in which states cannot maintain or demand absolute control.74 Additionally, there is no definitive understanding of how far a state’s “territory” extends in cyberspace. Even if there were, the obligation to respect state sovereignty may merely be co-extensive with the prohibition on intervention, given that non-intervention is a direct corollary of state sovereignty.75
Far more troublingly, historical practice weighs against any notion of an absolute right of sovereignty in cyberspace.76 For centuries, states have remained passive about establishing a legal regime to deal with routine intrusions into state sovereignty, most notably intrusions in the form of covert action77 and espionage.78 Similarly, most states have been unwilling to accept a rigid ban on all cross-border cyber infringements. In part, this is because a ban might limit their own cross-border covert intelligence, foreign political funding, and even cyber activities.79 In addition, a definition of sovereignty that is too broad might inadvertently cover a whole host of cross-border intrusions accepted in an interconnected world, such as the extraterritorial effects of a state’s telecommunications, industrial, monetary, and environmental activities. At the same time, subsuming all low-intensity cyber attacks into the dark netherworlds of the legally unclear category of espionage would reflect a total inability of international law to prevent or even to provide redress for the resultant damages.
Given this apparent gap for low-intensity cyber attacks in international law, it appears less surprising that Secretary Kerry condemned North Korea for the Sony attack by vaguely stating that North Korea had “violated international norms,” but without expressly referencing any violation of international law.80 Similarly, President Obama simply called North Korea’s attack “cyber vandalism,” a term without any international legal meaning.81 In this way, the State Department seemed to acknowledge the existence of such a gap, reflecting the State Department’s focus on cyber attacks constituting a use of force.82
ii. Liability in International Law
In light of these challenges, this Part argues that there is not actually a severe non liquet in international law for cyber attacks that cause serious harm but fail to qualify as intervention and use of force. However, identifying state duties to address low-intensity cyber attacks requires turning away, at least initially, from the traditional concept of “wrongfulness” as affirmed in the Draft Articles on State Responsibility and toward the concept of “liability” in international law. This Part establishes the origin and nature of transboundary liability, the duties and standards that it entails, and the relationship between a liability-based regime and the customary international law doctrine of state responsibility.
A. Liability and the Duty To Prevent and Redress Transboundary Harm
Historically, the duty to prevent and redress transboundary harm has roots in the Roman law maxim of sic utere tuo ut alienum non laedas, which states thateach must use his property in a way that does not cause injury to another’s.83 This notion underlies the law of nuisance recognized in many legal systems around the world.84 For example, English common law has long imposed a duty on property owners not to cause a nuisance that infringes upon another’s use and enjoyment of his land.85 French law similarly regards nuisance as the idea that “[n]o one may cause an abnormal degree of inconvenience in the neighborhood.”86
At common law, public nuisance may be considered a criminal wrong and require a showing of infringement on property beyond that which is generally “suffered by the public.”87 In contrast, liability for private nuisance has long attached even where the defendant has used his land lawfully.88 In these instances, liability results from a property owner’s activities giving rise to “encroachment,” “damage,” or undue interference with a neighbor’s “comfortable and convenient enjoyment of his land.”89 In other words, “[i]t is sufficient in such cases for the victim to show the inconvenience and its abnormal character”; the plaintiff need not establish harm resulting from an act of negligence.90
In international law, the paramount case proclaiming liability for the duty to prevent and redress transboundary harm is the 1941 Trail Smelter arbitration between the United States and Canada. In assessing damages to the United States from sulfur dioxide pollution caused by a Canadian smelter, the tribunal held that “under the principles of international law...no State has the right to use or permit the use of its territory in such a manner as to cause injury by fumes in or to the territory of another or the properties or persons therein.”91
Over the decades, the ICJ has also invoked the duty to prevent and redress transboundary harm on several occasions, mainly with respect to transboundary environmental damages. In its 1996 Advisory Opinion to the UN General Assembly on the legality of the threat of using nuclear weapons, the ICJ recognized “[t]he existence of the general obligation of States to ensure that activities within their jurisdiction and control respect the environment of other States or of areas beyond national control,” and noted that such an obligation is “now part of the corpus of international law relating to the environment.”92 The duty to prevent and redress transboundary harm has since played a role in a number of ICJ cases, including the court’s 1997 Gabčíkovo-Nagymaros Project (Hungary v. Slovakia) judgment,932010 Pulp Mills on the River Uruguay (Argentina v. Uruguay) judgment,94 and 2015 Certain Activities Carried Out By Nicaragua in the Border Area (Costa Rica v. Nicaragua) judgment.95
Several settlements for liability for the duty to prevent and redress transboundary harm have also taken place without much controversy. These include the 1957 Lac Lanoux Arbitration between France and Spain96 andthe Lake Ontario Claims Tribunal established in 1965,97 as well as dozens of arbitrations before ad hoctribunals covering issues ranging from oil spills and factory pollution to damages caused by altering watercourses.98
While international tribunals have frequently addressed liability for transboundary harm in the environmental context,99there is no reason why liability cannot be applied to transboundary harms in other settings.100 Indeed, history supports the application of liability for transboundary harm outside of the environmental context. Since the seventeenth century, scholars have recognized a duty to remedy cross-border harm in a variety of contexts. Grotius stated that from any “Fault or Trespass there arises an Obligation by the Law of Nature to make Reparation for the Damage, if any be done.”101 Even in his time, international law seemed to recognize a practice akin to liability: if one state owed tortious damages to another, the state’s failure to remedy the harm could be a just cause of war itself.102 For instance, states whose commercial vessels were damaged by foreign ships could demand compensation not only from the owners of the ships but also from the flag states of the foreign ships as well. Remnants of this practice persist today. In 1971, Liberia accepted liability when the Liberian tanker Juliana ran aground off the coast of a Japanese island.103 Likewise, in 1972, Canada cited Trail Smelter to remind the United States of its obligations when an oil tanker spilled near the state of Washington and polluted Canadian beaches.104
Over the course of the twentieth century, interest developed in clarifying how international law applies to the increasing number of harms made possible by the advancement of technology and growing interconnectedness of society.105 In 1956, the International Law Commission (ILC) took up the project of codifying the law of state responsibility.106 Though the project sought to define responsibilityfor wrongful international acts, there emerged an understanding that the “absence of wrongfulness [should] not prejudice compensation for damages caused by states to one another.”107 Based on this logic, the UN General Assembly invited the ILC in 1977 “to commence work on the topic of international liability for injurious consequences arising out of acts not prohibited by international law.”108 Since then, the ILC has produced dozens of reports on the topic of liability, including the 2001 Draft Articles on Prevention of Transboundary Harm from Hazardous Activities.109 While the ILC project ultimately dissolved, its conclusion with respect to liability remains relevant today:110 where an activity “give[s] rise to loss or injury” across state boundaries, “reparation [is] due” unless the harm has long been tolerated “in accordance with the shared expectations of the States concerned.”111
No doubt the capacity of humans to cause catastrophic harms beyond traditional state boundaries in an increasingly interconnected world heavily influenced the drafters of these ILC reports.112 Yet while flood damage, pollution, mine explosions, and nuclear radiation are frequently discussed by the working group,113 ILC Special Rapporteur Robert Quentin-Baxter noted that there was “never an intention to propose a reduction in the scope of the topic to questions of an ecological nature, or to any other subcategory of activities involving the physical uses of territory.”114
Outside of the ILC process, several prominent cases have appeared to apply transboundary liability in non-environmental contexts. In the 1948 Corfu Channel case, the Permanent Court of International Justice (PCIJ) held Albania responsible to the United Kingdom for mines laid in violation of “[e]very State’s obligation not to allow knowingly its territory to be used for acts contrary to the rights of other States.”115 When read closely, it appears that the court recognized the novelty of transboundary liability, particularly liability for military-like actions outside of the context of war, but applied it nonetheless—even to non-environmental damages. As it explained, the duty not to cause harm to another state is expansive in contemporary society; in fact, it is a duty “even more exacting in peace than in war.”116 Scholars have suggested that Corfu Channel recognized a “basic” transboundary duty upon states in international law “not...to act as to injure the rights of other states.”117 Indeed, building on Corfu Channel, several states have successfully sought compensation for transboundary harm from weapons tests.118
B. Liability and the Articles on State Responsibility
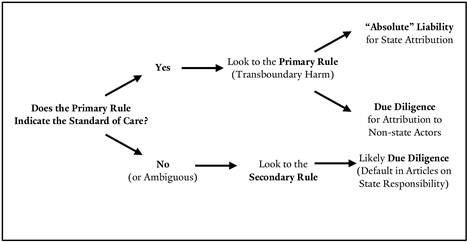
In light of this international practice, why is an act of transboundary harm not “wrongful,” and how is liability different from state responsibility? This Section explains that when transboundary harm occurs as the result of an otherwise lawful activity, a state may become liable to compensate the injured party for any harm caused. At that point, the state has not yet violated an obligation of international law; however, if the state fails to pay reparations, it becomes responsible for violating the duty to prevent and redress transboundary harm.
First, we must distinguish between primary and secondary duties (also referred to as “rules” or “obligations”) in international law.119 Primary duties govern state conduct. An example of a primary duty is the prohibition against intervention. Secondary duties impose remedial obligations on states for acts that violate a primary duty and are attributable to the state, taking into account pertinent circumstances and defenses (such as duress and necessity).120 An example of a secondary duty is the requirement to make reparations. Primary duties typically arise from treaties, customary international law, or general principles of international law, while secondary duties are often found in the Draft Articles on State Responsibility.121 Therefore, to understand when a state has committed a “wrongful act,” one must first turn to the primary duty in question and determine whether it has been breached.
Liability differs from the traditional concept of responsibility. According to the Draft Articles on State Responsibility—the primary restatement of the doctrine of state responsibility, prepared by the ILC—a state is responsible for an act (or omission) when the act is attributable to the state and wrongful under international law. An act is wrongful under international law when it is a violation of a state’s primary duty to another state.122 In contrast, liability does not result from a wrongful act per se123 but instead focuses on compensation for harms.124 Under this second approach, a state can be liable for an act of transboundary harm, even if the activities giving rise to the harm were not in themselves breaches of international law.125
Within this two-tiered system of state responsibility, the duty to prevent and redress transboundary harm is unusual, because it appears to contain aspects of both a primary and a secondary duty. As a primary duty, it incorporates the standards of care expected of states to fulfill the duty.126 Yet like a secondary duty, it requires states to provide remedies when harms occur.127 This combination of duties comprises “liability” in international law.128 Liability is thus a “continuum of prevention and reparation” resulting from the underlying duty to prevent and redress transboundary harm.129
These distinctions have caused much confusion over the years, as scholars have debated whether transboundary harms automatically give rise to state responsibility instead of liability. As ICJ Judge Higgins explains, “Cases like Trail Smelter—which we had all in our youth thought [had] something to do with international responsibility for harm to your neighbour (and a clear example of the absence of need of malice, or culpa),” are instead “not now questions of state responsibility but are put into another category”—what today is called international liability.130
Though distinct from responsibility, liability remains connected to responsibility in an important way. While causing transboundary harm is not prohibited by international law, “responsibility attach[es] for harm, [when] coupled with a [state’s] failure to meet the required standard of care.”131 As Judge Higgins explains, “[F]ailure to meet [the applicable] standard of care, with resultant harm—thatis the internationally wrongful act, for which state responsibility attaches.”132
Cases like Trail Smelter and Corfu Channel can be seen as imposing state responsibility after the state that caused transboundary harm failed to redress the situation. These cases typically involve states that failed to terminate and compensate for activities resulting in cross-border harm even after having received notice. Moreover, these cases involve transboundary harms resulting from activities that are not themselves unlawful under international law. Therefore, although some see Trail Smelter and Corfu Channel as establishing the idea that transboundary harm is wrongful under international law,133 these cases are better understood as invoking the concept of wrongfulness for transboundary harm only afterthe initial harms are inadequately redressed.
Under customary international law, states have long refrained from judging certain kinds of cross-border damages as wrongfulin and of themselves—provided that the state causing the damage takes remedial action to compensate for the damage.134 Under this liability regime, the state causing the transboundary harm must fail to provide redress beforethe injured state can invoke state responsibility. Until this point, the transboundary harm is not yet a “wrongful act” and the injured state cannot engage in countermeasures. This conception of liability helps prevent routine cross-border harms, especially unintentional harms, from escalating within the international legal system.
C. Dual Liability Standards
Even once we recognize that international law can impose liability for transboundary harms, we must decide what standard of care should be used to determine whether a state is liable. The Draft Articles on State Responsibility deliberately do not provide guidance as to the appropriate standard of care in any particular context.135 Instead, the Draft Articles on State Responsibility defer to primary rules to determine whether “some degree of fault, culpability, negligence or want of due diligence” applies in assessing state conduct.136 This is a sensible approach because, as Judge Higgins suggests,
[t]he standard by which the duty of care in regard to an obligation is to be tested is determined by reference to the particular requirements of that obligation. The law of state responsibility does not tell us the answer to this: we can say only that a state is responsible for failing to take, either generally or with respect to the conduct of individuals, duly diligent care or care to such other standard as the particular obligation requires.137
While some suggest that the Draft Articles on State Responsibility impose negligence as a default standard of care when the primary rule is unclear about the applicable standard of care,138 many primary duties require stricter or more lenient standards of care.139
The ILC suggests that the duty to prevent and redress transboundary harm is one such primary duty—in certain circumstances, it may impose strict or absolute liability. Strict liability is liability without fault, meaning that liability is imposed on the actor regardless of whether reasonable care was exercised.140 While similar, absolute liability imposes liability regardless of the actor’s potential defenses or intent.141
As Justice Blackburn explained in Rylands v. Fletcher, industrial society has recognized the need for strict liability for “anything likely to do mischief if it escapes” and “which [the owner] knows will be mischievous if it gets on to his neighbor’s [property].”142 Based on this reasoning, domestic jurisdictions throughout the world, as well as international treaties, recognize liability without “fault” for “abnormally dangerous” or “ultra-hazardous” activities, often in the areas of nuclear energy, transportation of hazardous chemicals, environmental damage, pollution, oil spills, train wrecks, space objects, and mining.143
Some have even suggested that absolute liability might apply beyond this practice to inherently hazardous activities. For example, Canada referenced absolute liability as a “general principle” of international law in its claim against the Soviet Union for damages caused by the “Cosmos 954” satellite.144 Similarly, the ILC has suggested that in some areas, states have been held liable for harms even when they took care to prevent them.145 Malcolm Shaw explains that the key benefit of the absolute liability approach is that it “mov[es] the burden of proof and shift[s] the loss clearly from the victim to the state,” as a plaintiff need not show that a state causing harm actually acted imprudently but only that harms emanated from its activities or territory.146
Nevertheless, the ILC acknowledges that most domestic legal systems have increasingly imported the concept of negligence into nuisance doctrine, and therefore that the duty to prevent transboundary harm is better seen as imposing a negligence standard.147 Negligence is defined as failure to behave with the level of care that a reasonable person would have exercised under the circumstances.148 The concept of negligence finds its way into international liability in the form of the standard of due diligence, which requires states to act with care that “is generally considered to be appropriate and proportional to the degree of risk of transboundary harm in the particular instance.”149 In the Pulp Mills case, the ICJ referred to the PCIJ’s judgment in Corfu Channel150and recognized “an obligation [on states] to act with due diligence in respect of all activities which take place under the jurisdiction and control of each party.”151 The court further explained due diligence as
an obligation which entails not only the adoption of appropriate rules and measures, but also a certain level of vigilance in their enforcement and the exercise of administrative control applicable to public and private operators, such as the monitoring of activities undertaken by such operators, to safeguard the rights of the other party.152
Yet it remains unclear which of these two standards is most appropriate for the duty to prevent transboundary harm. Negligence has been found alternatingly essential and irrelevant to liability for transboundary harm in different cases.153 There is also extensive disagreement over how to interpret the few cases that have dealt explicitly with transboundary liability. For instance, some observe that because the United States did not “affirmatively prove the defendant’s negligence or wilful default” in Trail Smelter,strict liability effectively applied.154 Others make a similar argument with respect to the Lake Ontario Claims Tribunal, arguing that the Tribunal made no express finding of fault or negligence for the damages that resulted from extensive flooding in connection with a Canadian-built dam.155
Disagreement also persists over the standard applied by the ICJ in Corfu Channel. The most persuasive views, supported by the dissents of Judges Badawi Pasha and Winiarski, suggest that Corfu Channel stands for strict liability in certain situations, given that the breach of the duty to prevent transboundary harm was recognized without proof of negligence.156 The dissenting judges argued that Albania had neither breached any duty of diligence nor acted with willful default, and instead that the court had applied a higher standard, what they called “absolute” liability.157
A way out of this dissensus can be found in Nuclear Tests (Australia v. France).158In the ICJ hearings in the case, Australia argued that there is a growing trend toward a due diligence standard for activities holding societal value,159 but strict liability for those imposing unreasonable risks without clear benefits. While “every transmission by natural causes of chemical or other matter from one State into another State’s territory, air space or territorial sea automatically created a legal cause of action in international law without the need to establish anything more,” contemporary state practice has in fact “modified the application of this principle in respect of the interdependence of territories.”160 Therefore, in Australia’s view, liability standards should be more lenient when the activities causing harm “are generally regarded as natural uses of territory in a contemporary society and...while perhaps producing some inconvenience, they have a community benefit.”161 The ICJ seemed to adopt this approach in Nuclear Tests when it found France’s activities to have “no compensating benefit to justify New Zealand’s exposure to such harm.”162
Therefore, we can reconcile these competing standards by recognizing that while private nuisance has long looked favorably upon absolute liability for otherwise “abnormal” activities that do not benefit the community, due diligence has been more accepted for activities that cause harm but are thought to promote a common good. A dual approach of this sort recognizes that not all transboundary harms exist in the same light, particularly if imposing absolute liability would result in onerous burdens or infringements on other important principles, such as privacy and open internet access. This approach is particularly apt for the cyber context, as discussed next.
figure 2.
standards of liability and responsibility under international law
iii. Applying Liability for Transboundary Harm to Low-Intensity State-Sponsored Cyber Attacks
“[W]e are confident the North Korean government is responsible for this destructive attack . . . . If [they want] to help, they can admit their culpability and compensate Sony for the damages this attack caused.”
–Mark Stroh, National Security Council Spokesman163
This Part applies the concept of liability to low-intensity state-sponsored cyber attacks and discusses how the appropriate standard of care should depend on whether a cyber attack is attributable to a state or non-state actor.
A. Contemporary Approaches and Cyber: An Absurd Result?
164Recent scholarship has begun to import features of the duty to prevent transboundary harm into the cyber context.165 Most notably, this concept surfaces in the Tallinn Manual.166 Some have suggested that states have a “due diligence obligation with respect to both government and private cyber infrastructure on, and cyber activities emanating from, their territory.”167 In this framing, a state that fails to meet this due diligence standard of care is held responsible under international law and may be subject to countermeasures.168
Beginning with the issue of transboundary harm, the Tallinn Manual suggests that due diligence is either itself a primary obligation in international law, or else a standard of care owed with respect to the principle of territorial sovereignty.169 Michael Schmitt is equally vague; for him, due diligence is a “principle” of international law on its own but at the same time, one that “derives from the principle of sovereignty.”170
To consider due diligence to be a primary obligation is problematic. Due diligence appears to exist not as an independent obligation within customary international law, giving rise to state responsibility, but instead as a standard of care owed with respect to certain primary duties in international law.171 But the second option—deriving a due diligence standard from the principle of sovereignty—may also present challenges, particularly in the cyber context. For one, as Part I discussed, considerable issues arise in attempting to apply the notion of sovereignty to cyberspace. Not only is it difficult to determine the extent of a state’s sovereign territorial rights in the internet, but there are also significant arguments against an absoluteright of states to sovereignty in the first place. Moreover, critics point to hundreds of years of state practice suggesting that interferences below a certain level of coercion are tolerated—or at least not clearly unlawful—as in the case of espionage.172
Yet even if we were to accept that a due diligence obligation attached to the principle of sovereignty, this approach would create significant conflicts with other legal constructs. For example, this approach would render the concept of intervention redundant; indeed, non-intervention might not make sense at all. After all, why would the prohibition on intervention be limited to coercive intrusions on a state’s sovereign affairs if there already exists a duty of due diligence upon states to avoid all intrusions?
Though these differences might seem trivial, the consequences are not, especially in the context of low-intensity cyber attacks. For example, it is likely that states possess a due diligence obligation to prevent cyber attacks that constitute a use of force or intervention, since these are two categories where the primary duties prohibiting these acts may expressly incorporate a standard of due diligence.173 However, it is less certain that due diligence attaches for cyber attacks below this level. For these attacks, one must turn to the relevant primary duty. In the case of low-intensity cyber attacks, this is the duty to prevent and redress transboundary harm. If due diligence is the appropriate standard by which to judge state conduct at the level of low-intensity cyber attacks, then such an approach would have to recognize the underlying duty to prevent transboundary harm—given that this is the only primary duty that governs the low-intensity space.174
This leads us to the next set of questions: how far liability for the duty to prevent transboundary harm extends and what standard of care it calls for. Despite relying on Trail Smelter and Corfu Channel, both Schmitt and the Tallinn Manual avoid addressing this set of questions.175
By only referencing due diligence, Schmitt and the Tallinn Manual avoid addressing whether states have an obligation not to launch cyber attacks outside of the context of non-intervention and use of force. When the duty is framed just in terms of due diligence, states appear to have only a positive duty to thwart other actors from using state territory to launch attacks. As the Tallinn Manual indicates, a state may not “allow knowingly its territory to be used for acts contrary to the rights of other States,”176 and as such, “[s]tates are required under international law to take appropriate steps to protect those rights.”177 The Tallinn Manual goes so far as to suggest that due diligence applies to cyber attacks “launched from cyber infrastructure that is under the exclusive control of a government.”178
Stepping back, these statements seem to be a relatively backwards way of getting at a more important idea: whether states owe not just positive duties to prevent attacks, but also negative duties to refrain from them. International law typically imposes a negative duty not to act in a certain way—such as a duty not to launch a cyber attack—before it imposes related positive duties to act—such as a duty to prevent others from launching a cyber attack. Accordingly, states are usually held responsible after violating not just positive duties but also negative duties.179
B. Applicability to Low-Intensity State-Sponsored Cyber Attacks
I contend that (1) the relevant duty for low-intensity cyber attacks is the duty to prevent and redress transboundary harm and (2) this duty applies to all transboundary cyber harms above a minimum level of tolerance—including those that are intentionally caused by states. I propose associating the duty to prevent and redress transboundary harm with two standards of liability: absolute liability for attacks attributable to a state and due diligence for attacks by actors operating within a state’s boundaries.180 This dual-standard approach recognizes that positive and negative duties impose different burdens on states. While it is considerably more difficult for states to prevent non-state actors from launching an attack, states clearly have the ability not to launch attacks in the first place.
State-sponsored cyber attacks appear to meet the description of activities traditionally governed by absolute liability. Even the best-designed attacks carry a risk of damage to unintended parties, given the interconnectivity of the internet.181 This militates in favor of considering state-sponsored cyber attacks to be essentially “abnormally” dangerous or “ultra-hazardous” activity for the purposes of liability.
figure 3.
two standards of liability for low-intensity cyber attacks
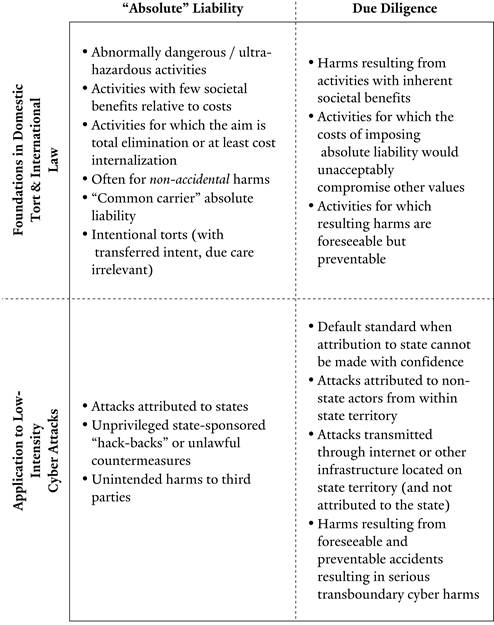 |
The intentional nature of state-sponsored attacks supports absolute liability as the applicable standard of care, at least when attribution is possible. Typically, actors who commit intentional torts are liable for all directly consequent harms, regardless of the degree of care exercised or the extent to which the subsequent harms were foreseeable or intended.182 For example, if a defendant intends to hit A and unintentionally hits B as well, the defendant is liable for damages caused to both A and B, even if the defendant was theoretically “diligent” in his or her attempt to hit A and not B.183 This doctrine, known as the principle of transferred intent, imposes what amounts to absolute liability for intentional torts so as to discourage tortious conduct and to make whole each impacted party.184
By contrast, where attribution to a state is impossible, but attribution to private entities operating within a state’s territory or via infrastructure located in a state is possible, an attack should only give rise to liability if the state failed to act diligently in preventing it. That is, the applicable standard of care imposed upon states in these cases should be due diligence. This obligation encourages states to take measures to prevent cyber criminals from operating within their territory. It also decreases the likelihood that states will escape liability for attacks that they launch but that are difficult to attribute to them, since due diligence will serve as the default standard of care. This approach is similar to the one proposed by Schmitt and the Tallinn Manual:
[T]he due diligence principle . . . provide[s] grounds for a response when a state is suspected of engaging in the hostile cyber activities, but insufficient evidence exists to satisfy the level of certainty necessary for legal attribution. In other words, even where there is no smoking gun that would legally justify treating the cyber operations as those of the state, the state could be treated as having failed its due diligence obligation, and the principle would permit countermeasures on that basis.185
Yet in sharp contrast to the approach taken by the Tallinn Manual, a breach of the duty to prevent and redress transboundary harm should not give rise to state responsibility directly, but instead should result first in liability—that is, a requirement that the state compensate for the damages it caused. Liability, as opposed to responsibility, is particularly appropriate given the immense challenges of adequately assessing state actions,186 as discussed in the next Part. This approach would also require states not simply to fire back countermeasures, but indeed to seek compensation through a liability claim before resorting to a claim that the attacking state should be held responsible.
In sum, the purpose of imposing either absolute liability or the due diligence standard of care should be to compel states to compensate for the damages caused by cyber attacks, as well as the damages caused by their inadequate monitoring and security of their domestic systems.
C. Complications of a Liability System
This Section considers potential issues with applying liability for transboundary harms to low-intensity cyber attacks, including whether the intentional nature of low-intensity cyber attacks prevents an application of liability, what level of damages can give rise to liability, and the mechanisms that might be invoked to impose liability.
1. The Issue of Intent
One might suggest that the duty to prevent and redress transboundary harm should turn on the issue of whether the state intended to cause the harm, but international law and precedent counsel otherwise. International tribunals have not held that intent precludes liability for the duty to prevent and redress transboundary harm.
For example, international law is often reluctant to pass judgment on the “mindset” of a state, particularly given uncertainty as to determining the intent of an expansive state apparatus.187 In response to the puzzle of determining a state’s “intent,” effects-based assessments have gained prominence over the years. Under an effects-based assessment, a state may incur responsibility even when it unwittingly engages in certain prohibited or harmful activities.188 The UN International Group of Governmental Experts adopted such an “objective” approach for cyberspace, defining a cyber “armed attack” by the size and scale of damages involved, without reference to the state’s “intent.”189
If intent is not necessary in these cases, it would be unreasonable to require intent in the low-intensity cyber realm in order to hold a state liable for transboundary harm. After all, liability is less serious than responsibility, given that an injured state would make a liability claim against the attacking state beforeasserting that the attacking state should be held responsible,190 and a liability claim does not permit injured states to take advantage of countermeasures, as responsibility frequently does.191
Perhaps the strongest argument for deeming intent irrelevant comes from the fact that a low-intensity attack is a per senegligent act, given the broader duty on states to prevent and redress transboundary harm. For example, the ILC conceives of the duty as encompassing a duty not only to perform risk assessments and to minimize risks of harm in prospective activities, but also to give notice and stop harm once the state becomes aware of it.192 In this sense, once a state knows it is causing harm—even if it did not realize that its cross-border actions would do so at the outset—it has a duty to stop and redress the situation and to compensate injured parties for any harms caused.
International law has been quick to apply liability for “non-accidental” torts—that is, torts that are caused despite a state’s awareness of harmful effects mounting over time.193 In some senses, low-intensity state-sponsored cyber attacks resemble such “non-accidental” torts, and states are thus best held to a stricter standard of care—what I propose to be absolute liability—to be associated with the duty to prevent and redress transboundary harm.
2. Scale of Damages
Although a comprehensive discussion of damages and how courts should calculate them is beyond the scope of this Note, two issues merit attention here: whether liability can only be applied in the context of cyber attacks that result in physical damage and whether liability is likely to lead to claims that are too insignificant.
First, liability for the failure to prevent and redress transboundary harm need not be limited to instances of physicaldamage, so long as any nonphysical damage is of a degree not normally tolerated and not frivolous or trivial.194 Domestic tort law includes many examples where liability for nuisance—a concept similar to the duty to prevent transboundary harms—has been applied to nonphysical territorial intrusions.195 Similarly, international law has addressed nonphysical harm in disputes over radiation exposure from atmospheric weapon tests.196
Second, although some might be concerned about de minimisclaims being brought, market forces are likely to dissuade plaintiffs from asserting claims that are unlikely to result in significant awards. Applying liability to the duty to prevent and redress transboundary harm would also deter de minimis claims, since a court would balance other societal considerations and equitable interests. Additionally, tort law and the concept of liability are more amenable than the doctrine of state responsibility to the idea of mitigation of damages, which would help limit the problem of unreasonably large claims. Unlike state responsibility, liability for transboundary harm is not concerned with per se violations of particular principles or prohibitions.197 The Draft Articles on Transboundary Harm specifically call on states to cooperate in good faith to “minimi[ze] the effects of the risk.”198 When applying societal concerns and engaging an “equitable balance of interest” to determine liability, the Draft Articles on Transboundary Harm asks courts to weigh “the economic viability of the activity [causing harm] in relation to the costs of prevention demanded by the states likely to be affected.”199 Liability, in other words, entails a consideration of reasonable harm prevention by both parties.
Relatedly, liability for the duty to prevent and redress transboundary harm applies only to harms not encompassed by the practices of mitigation and prevention.200 The Draft Articles on Transboundary Harm suggest that tribunals evaluating claims of transboundary harm consider “the degree to which the states likely to be affected are prepared to contribute to the costs of prevention,” “the standards of protection which the states likely to be affected apply to the same or comparable activities,” and any standards “applied in comparable regional or international practice.”201 This means that liability is less likely when applied to harms that have become routinely tolerated internationally, even if not accepted. Thus, cyber attacks that are considered routine acts of espionage would fall outside the scope of liability, since espionage has been tolerated by the international community for some time.
However, as global norms develop toward states reasonably protecting their infrastructure against cyber attacks, liability should not arise for harms to states that take unreasonably limited efforts to protect themselves.202 For example, as Obama Administration’s report on cyberspace stated, “[S]tates should recognize and act on their responsibility to protect information infrastructures and secure national systems from damage or misuse.”203 But requiring only reasonable mitigation and prevention makes sense as states cannot possibly prevent all domestic cyber harms from foreign sources.
Although identifying the type of low-intensity cyber attack that would go beyond a state’s baseline duty to protect itself is challenging, the State Department has made one threshold clear: North Korea’s attack on Sony. In the words of one senior official, the Sony attack “clearly crossed a threshold” from “website defacement and digital graffiti” to an attack on IT infrastructure.204 In the State Department’s view, this attack fell beyond the bounds of reasonable mitigation and prevention, and thus should have given rise to state liability. While it may be too early to tell, some states seem willing to accept, or at least acquiesce to, this view.205
3. Enforcement
Though enforcement is always a challenge in international law, several characteristics of liability for transboundary harm make it a desirable way to regulate low-intensity cyber attacks: (1) diplomatic protection and settlement through ex gratia claims, (2) formal international legal claims, and (3) domestic suits under exemptions to foreign sovereign immunity. In this way, liability for transboundary harm proves effective for combating low-intensity cyber attacks, particularly in light of the alternatives discussed in Part IV.
Turning first to diplomatic protection, the history of international law is replete with examples of states taking action at the interstate level on behalf of citizens whose persons or property have been mistreated by another state. As Emmerich de Vattel recognized in 1758, “[W]hoever ill-treats a citizen indirectly injures the State, which must protect that citizen.”206 Today, international investment law frequently deals with the issue of holding a state liable for harms caused to private actors. As the tribunal in Mavrommatis Palestine Concession explained, the act of a state taking up claims to “obtain satisfaction” on behalf of its subjects injured by or in a foreign state is an “elementary principle of international law.”207
A state’s espousal of a “claim of its citizen against the offending government” is known as “diplomatic protection.”208 For instance, diplomatic protection would involve a state asserting a claim on behalf of one of its nationals against a foreign state when the individual was harmed in the foreign state.209
In contrast to classical diplomatic protection, diplomatic protection for transboundary harms is in a sense “reverse” diplomatic protection: states make claims on behalf of their nationals who are injured within their own borders by foreign states, not outside of them. Indeed, states routinely make informal attempts at protection for harms to property or interests in their territories.210 In the context of transboundary harm, states have most frequently achieved such protection by negotiating claims of voluntary payments, also known as ex gratia payments in international law.211
Framing claims in international legal terms helps to create a common language on which to premise negotiation of voluntary settlements in the first place.212 Tethering claims to underlying legal considerations may also encourage settlement by supplying legitimacy and lawful authority to states exercising diplomatic power.213
Ex gratia compensation may be particularly effective in the cyber context because it permits states to redress harms without having to acknowledge wrongdoing or causation. This can be useful when a state seeks redress for transboundary harms caused by a state that may be reluctant to acknowledge fault or causation. Such was the case when the United States, avoiding recognition of fault, compensated island nations harmed by nuclear weapons tests.214
In cases where voluntary compensation does not take place, international courts can provide an arena for hearing liability claims for violations of the duty to prevent and redress transboundary harm. The ICJ could provide a forum for formal claims of diplomatic protection for injuries caused to its citizens and private industries through low-intensity cyber attacks. In recent years, Argentina and Costa Rica have both invoked transboundary harm before the ICJ in the context of cross-border environmental damages.215 In addition, states have made a variety of diplomatic protection-type claims before the ICJ on behalf of their nationals. In the Diallo case, for instance, Guinea sought relief for the violation of the human rights of its nationals by the Democratic Republic of the Congo.216
The Permanent Court of Arbitration could serve as another setting for settling transboundary harm claims stemming from low-intensity cyber attacks. Some states may be willing to submit to arbitration for even very contentious matters after some time has passed. Though states often refuse to proceed to arbitration (or even negotiations) immediately, changes in political circumstances may open up room for arbitration eventually. The unusual Rainbow Warrior case illustrates this phenomenon: France ultimately agreed to arbitration over damages resulting from its intelligence service blowing up a Greenpeace vessel.217
Finally, many governments have also recognized liability in theirowncourts for tort claims against foreign states. This could serve as an additional option for providing redress for low-intensity cyber attacks. Although foreign sovereign immunity may bar certain claims, customary international law on sovereign immunity may contain an exception for “territorial torts” committed by one state that affect another state’s territory.218 In fact, the UN Convention on Jurisdictional Immunities of States and Their Property has affirmed such a principle.219 Guided by this logic, Greece has permitted suits against Germany for tortious injuries and damage sustained on Greek territory during World War II, and Italy has refused to recognize sovereign immunity as barring claims for similar tortious acts committed by Germany on Italian territory.220
In the United States, the Foreign Sovereign Immunities Act explicitly codifies such an exception to sovereign immunity for torts carried out on U.S. territory—including for a wide variety of activities “in which money damages are sought against a foreign state for personal injury or death.”221 Relying on this exception, in Letelier v. Republic of Chile, a federal court denied sovereign immunity to Chile when Chilean officials detonated a car bomb in Washington, D.C., in 1976.222 More recently, Congress has passed legislation that appears to broaden this exception and expand state liability to torts not entirely committed in the United States.223
In this way, recognizing transboundary liability would effectively open up two levels of redress: first, through liability—including claims heard either domestically or internationally—and, second, through international state responsibility in the event that attempts at compensation or settlement fail.224
iv. The Benefits of International Liability
This final Part considers the theoretical and practical benefits of recognizing liability for low-intensity cyber attacks. Transboundary liability not only offers a practical solution to the gap for low-intensity cyber attacks but also avoids many of the downsides of an expansive use of traditional international legal concepts.
A. Pragmatic Appeal to States and Emphasis on Redress
Low-intensity state-sponsored cyber attacks address situations where states are unlikely to agree to constrain their activities by overtly declaring such attacks wrongful. Serious enough to cause costly damage, though not quite expansive enough to meet the scale of a use of force or intervention, these attacks are increasingly becoming a literal “nuisance” in international law. And yet, as states increasingly come to see low-intensity cyber attacks as a valuable option in their foreign policy toolkit,225 it is difficult to imagine a world in which they will sign on to attempts to outlaw low-intensity cyber attacks completely, let alone accept the expansion of certain prohibitions (such as the use of force and intervention) to cover them. Liability for transboundary harm encourages states to internalize the costs of foreign harm associated with their cyber activities without requiring a new treaty or infringing upon other laws given its application only to actsotherwise not prohibited internationally.226
More importantly, there are persuasive reasons to resist declaring all low-intensity cyber attacks wrongful. As M.B. Akehurst explains, liability has several features that make it pragmatically preferable to responsibility:
[A] certain stigma attaches to the commission of an unlawful act. States may therefore be reluctant to pay compensation for wrongful acts because they are unwilling to admit that they have done anything wrong. They may be more willing to pay compensation for lawful acts, because such payments do not imply a confession of wrongdoing. A rule requiring payment of compensation for lawful acts “should make easier a just, effective and amicable settlement of any liability that may arise.”227
Moreover, the ILC has noted that accusations of wrongfulness may induce counterproductive antagonism instead of actual redress for injured parties.228
Greater antagonism would also result from taking any of the other approaches to addressing low-intensity cyber attacks. Expanding the definition of the use of force would allow states to label low-intensity cyber attacks as “armed attacks” and respond with force.229 Even declaring all low-intensity cyber attacks just to be violations of non-intervention and sovereignty would permit states to take excessive countermeasures under state responsibility. Alternatively, subsuming low-intensity cyber attacks into the legally unclear category of espionage would require states to accept significant damage from foreign covert action and international law would remain unable to address it. Categorizing these sorts of attacks as espionage would also permit states to conduct in-kind low-intensity counter attacks, provided that these, too, stay at the level of cyber espionage. Either of these approaches would also fail to compensate for certain harms to private actors, such as the tens of millions of dollars in damages to companies like Sony.
Approaches invoking state responsibility would present their own concerns. For instance, holding states responsible for too many cyber attacks might encourage states to impose draconian restrictions on internet use. Moreover, expanding preexisting categories of law to proscribe low-intensity attacks could create havoc in areas of law unrelated to cyber attacks. And broadening the concept of intervention or sovereignty could result in severe problems for NGOs and other supporters of human rights who engage in what might be called low-level coercive activity.230
In addition, it is difficult to justify imposing state responsibility directly in cases where it is unclear whether an attack inadvertently passed through a state’s borders due to the interconnectivity of the internet231 or has been inaccurately attributed.232 After all, responsibility is one of the most serious notions in international law and one that opens the door to ICJ and Security Council sanctions, outcasting, and remedies implicating a host of other legal rights and international obligations. Weakening or fundamentally altering state responsibility by creating a system that would be difficult to enforce or even comprehend in the cyber context would hardly be productive in the long term.233
In contrast, a liability approach, through its varying standards of care, can better account for low-intensity cyber attacks. Unlike an approach that invokes sovereignty or non-intervention, a dual liability regime provides a tailored approach to different cases depending on varying degrees of attribution. Similarly, liability takes into consideration varying degrees of reasonable conduct, particularly for attacks carried out by non-state actors via a state’s infrastructure.234 In addition, because liability works backwards from harm, as opposed to via an abstract principle for all breaches (intentional or not), it does not need to apply in all cases of theoretical injury to a state’s sovereignty.235 In this sense, liability supports a system where states are, even if not absolutely prohibited from launching attacks, at least compelled to account for damages and take reasonable steps to prevent cyber harms abroad.236
This proposed dual liability regime is even more attractive in light of another alternative: charging individual state officials or state-hired individuals for cyber harms (instead of states directly). For example, in March 2016, the United States indicted several Iranian state hackers for a range of cyber attacks on U.S. companies.237 Critics have rightly pointed out that these indictments may set a problematic precedent for U.S. officials traveling abroad.238 In certain cases, individual indictments can also divert attention away from the “true” source of liability: the state that actually ordered and developed the cyber attack in the first place. Even if a government could capture alleged cyber criminals, it would end up bypassing the party with “deeper pockets” that would be most able to change broad-ranging cyber policies.
B. Clarification of the Law of Countermeasures
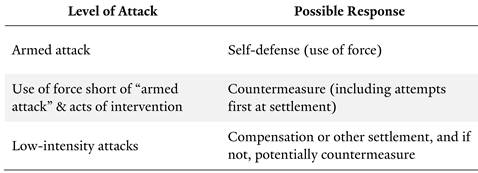
Recognizing transboundary liability also elucidates the duties of states engaging in increasingly common “hack-backs,” or what some refer to (sometimes incorrectly) as countermeasures.239 According to the Tallinn Manual, “a State injured by an internationally wrongful act may resort to proportionate countermeasures, including cyber countermeasures, against the responsible State.”240 Countermeasures are nonviolent actions taken in response to another state’s wrongful act241 in order to induce compliance with international law.242 However, under the Draft Articles on State Responsibility, countermeasures must be reversible “as far as possible,”243 proportionate,244 and can only be taken after demands for the cessation of the wrongful conduct fail.245
Recognizing the duty to prevent and redress transboundary harm and liability for low-intensity cyber attacks helps mitigate the problem of the overuse of cyber countermeasures, while at the same time not eliminating an important state tool. Liability requires states to seek settlement through compensation before engaging in any countermeasure.246 This requirement only amplifies what is already a condition inherent in the law of countermeasures: to first call on the state alleged to have caused harm to make reparations.247 If compensation for transboundary harm is not provided after a significant period of de-escalation and recourse to domestic and international legal processes for settlement, then a state may be held responsible, and countermeasures may be considered, as at that point a wrongful international act would have been committed.248
figure 4.
permissible international legal responses for cyber attacks, including under a liability framework
Another way of understanding the requirement to seek settlement before launching a countermeasure comes from the work of the ILC. The Draft Articles on the Prevention of Transboundary Harm from Hazardous Activities indicate that “states are to co-operate in good faith in trying to prevent such activities from causing significant transboundary injury” as well as in mitigating the “effects of the risk,” a notion that is also found in international environmental law.249 The benefits of this approach may be particularly important when it comes to the cross-border effects that could stem from a range of different activities in contemporary society, not all of which could give rise to countermeasures under an expansive definition of sovereignty. These notions also square well with the UN Charter, which calls on “parties to any dispute...[to] first of all, seek a solution by negotiation, enquiry, mediation, conciliation, arbitration, judicial settlement...or other peaceful means.”250
C. Recognition of Duties Owed to Third Parties
Finally, applying liability for transboundary harms to low-intensity cyber attacks may clarify obligations owed to third-party states. Commentators have struggled to articulate the obligations—if any—that states have to third parties when engaging in countermeasures.251 For instance, one line of analysis suggests that if a state launches a countermeasure against a second state and the countermeasure affects a third state, the third state has no recourse—unless the attack violates particular rights owed to that third state under a treaty.252
Recognizing the duty to prevent transboundary harm would affirm that liability fully extends to countermeasures affecting third parties. This is particularly important because cyber offenses are likely to cause unintended damages.253 For instance, as the former head of the National Security Agency has recognized, unlike traditional weapons, malware and other cyber weapons do not self-destruct upon impact.254 As a result, absent proper design, cyber weapons can effect repetitive damage that is far broader than intended. Liability is particularly equipped to deal with the problem of unintended consequences in cyber attacks. First, liability takes a somewhat less restrictive view of causation than responsibility.255 Second, liability, especially an absolute liability standard, emphasizes that states have strict duties to prevent all low-intensity harms to third states, regardless of whether the state launching the attack “took care” to guard against such third-party harms or intended to hit only one target.256
Recognizing liability for damages to third parties resulting from illegal hack-backs or lawful countermeasures also sheds light on another unresolved issue in the literature: whether states have a right to property in international law, and thus a right not to have their property or property in their territory damaged.257 While not answering the question directly, liability for transboundary harm suggests that low-level torts and cross-border property damages are not without limitation or redress in international law simply because they occur outside of armed conflict, intervention, or the use of force.
conclusion
Liability for the duty to prevent and redress transboundary harm can fill the gap in public international law for low-intensity cyber attacks. States are not only subject to the standard of due diligence in preventing transboundary cyber harms originating from non-state sources, but also subject to absolute liability in terms of refraining from causing harm through attacks themselves—even when these attacks are not otherwise outlawed directly.
Thus, I argue for an approach that avoids both expanding preexisting categories of wrongful state action and leaving all low-intensity cyber attacks outside of the fold of international law entirely. Liability for the duty to prevent transboundary harm not only encourages peaceful settlement and de-escalation, but also offers a more realistic approach for addressing the cross-border intrusions that are becoming increasingly common in the contemporary era.
